How to Identify Which Code Was Used to Encrypt
Some packers use common algorithms while others use custom code to compress andor encrypt files. You also will need an internet connection to be able to complete this tutorial.

How To Encrypt Strings Files In Your Source Code Dev Community
To accomplish this an ephemeral one-time 128-bit symmetric key is generated and is used to encrypt the message body using Salsa20 encryption algorithm.

. This process converts the original representation of the information known as plaintext into an alternative form known as ciphertextIdeally only authorized parties can decipher a ciphertext back to plaintext and access the original information. Below are all the bits and pieces that I used for setting up Lets Encrypt SSL on my Raspberry Pi. This ephemeral message key is then encrypted using each recipients session key.
To encrypt this message for every session with every device that the target user has. The proxy hides your IP address meaning the Lets Encrypt tool will fail to verify your Raspberry Pis IP address and generate an SSL certificate. In cryptography encryption is the process of encoding information.
They obfuscate file code making it very difficult to locate and analyze malware on your system. In any case the more you know about popular packers used in malware the more equipped you will be to identify and unpack malware in your own system.
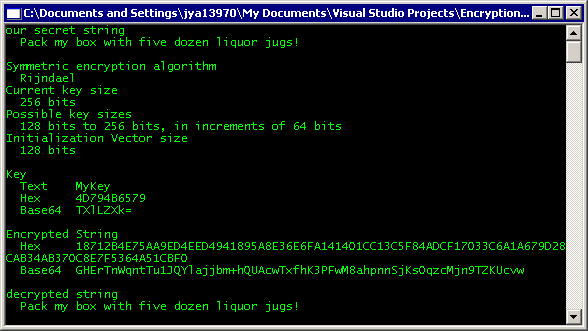
Net Encryption Simplified Codeproject

How To Encrypt Strings Files In Your Source Code Dev Community

The Display Of The Jpg File Binary Code Before Encrypted After It Is Download Scientific Diagram
Comments
Post a Comment